Introduction
The average business IT user accesses around 100 websites and applications that require passwords. These will range from critical business systems to shopping websites, school notifications, and TV subscription services.
Research shows that around 40% of businesses experience cyber breaches each year. The most common attack was phishing, the practice of sending emails to induce individuals to reveal personal information, such as passwords, bank or payment details, or other valuable data. The average cost of a compromise was £4,300 (source: Cyber Security Breaches Survey 2022 – GOV.UK (www.gov.uk))
Separate research indicates that around 80% of breaches are due to poor or reused passwords (source: LogMeIn: Poor Or Reused Passwords Responsible For 80 Percent Of Breaches | CRN)
Therefore, businesses and charities must have a strong password and authentication policy to reduce their exposure to risk.
This article looks at four things your organisation should consider when defining a password policy.
Password length and complexity
The first part of the password issue is length and complexity.
The most common passwords reported are all incredibly basic; here are three sources of the top five passwords in use;
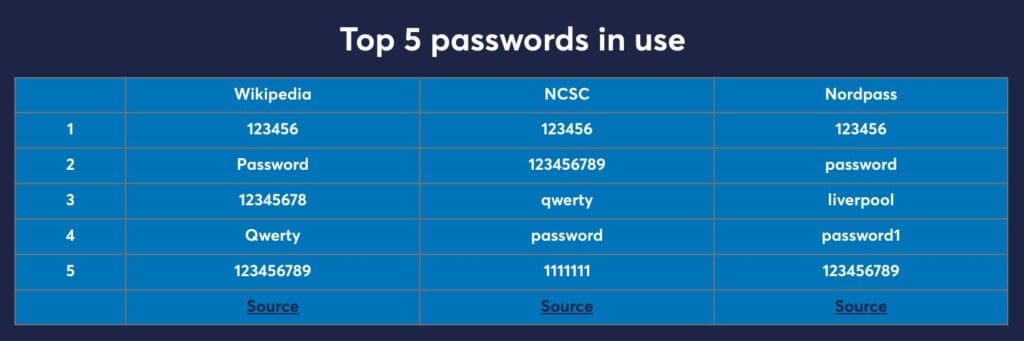
Password length is a much more significant deterrent to cybercriminals than complexity. On average, a 15-character lowercase password will take 100 years to break. At the same time, an eight-character password with numbers, lowercase, uppercase, and symbols will take just 39 minutes to crack.
The full table of times to break passwords is shown below.

Advice
This advice is counter to what is now an outdated recommendation to make a password strong by replacing letters with numbers or symbols. For example, you may have previously set a password as follows; Pa55w0rd – a password that would now take 31 seconds to break. This methodology makes it more challenging for people to guess passwords but makes no difference to the time it would take a computer running a brute force attack.
A brute force attack is performed by a computer that tries every combination of numbers, letters, and symbols until the password is guessed. At the extreme, if a password is only one character long, then the computer needs to make less than 100 guesses. A 15-character password has trillions of possible outcomes which will take the computer much longer to break.
In some circumstances, it’s possible to apply a lockout policy. This will lock an account for a period of time after a given number of guesses. For example, if a password is entered incorrectly five times, the account will be locked for 30 minutes. This system means that at most, only 240 guesses can be made in any 24-hour period. We use lock-out policies for network passwords for customers who operate a server. Even with a lock out policy, it only slows down the time taken to crack a password, so a long and complex password is still recommended.
In summary, a user should ensure they choose passwords that are at least twelve characters long, that include some complexity with at least numbers, upper case, and lower case characters.
They should not;
- Contain personal information such as birthdates, addresses, phone numbers, or names of pets, family members, friends or fantasy characters
- Contain work-related information such as the Company name
- Contain common patterns such as 123, qwerty, zxcv or 999.
- Contain common words or phrases such as ‘welcome’ or ‘password’, including variations such as ‘p@zzW0rd456’.
To make longer passwords memorable, the recommendation is to select three or four random words. For extra security the words can be interspersed with symbols or numbers.
For example, three random words may be; cabin, north, and sunny. It’s not hard to picture a sunny cabin located in the north. Intersperse that with a symbol of your choice, and suffix the password with a number and you have a very secure and memorable password; cabin$NORTH$sunny$66
If you need help generating a truly random password, try using a random password generator like XKPasswd – Secure Memorable Passwords
Unique
There are two common ways for passwords to become exposed.

The first is where the user gives the password to the cyber criminal. That’s more common than you may expect, and the very definition of a phishing attack.
A typical phishing email will be from someone you know, with the subject of ‘contract’, ‘remittance’, or similar term and will include a link or attachment. Clicking on this will prompt the user to enter their credentials to view the information, and hey-presto the password is given away.
Phishing is not limited to business settings. Your staff will be regularly exposed to attempts to give up their passwords in many scenarios; for example a fake email saying that a shopping account, or mobile phone contract, will be locked out if the password isn’t supplied. Phishing often injects urgency in to the required action. If the user doesn’t give up their information within a short time period of time their account will be locked, suspended, or deleted.
The second way passwords are exposed, is where large quantities of data are stolen from corporates. This data is then sold on, or uploaded to the dark web.
It is imperative that passwords are unique because even with the most stringent measures, any password can become exposed. One source estimates that over five billion passwords were stolen in 2021 alone; https://www.itgovernance.co.uk/blog/data-breaches-and-cyber-attacks-in-2021-5-1-billion-breached-records
Consider a user has signed up for a national shopping chain with an email address and password. The user has the same password for all their logins, including their email address. A cybercriminal has their email address; john.smith@personalemail.com and their shopping password. The first thing a criminal may try is to log in to that email address with the shopping password. If the user has just one password, their email account has now been exposed. Even if not, other shopping accounts may also have been exposed. What if the password is the same for their work email account; john.smith@yourcompany.com? Your business data is now exposed.

The best way to protect against this risk, is to ensure that every password is unique. Wherever possible set up Two Factor Authentication. We will be discussing this as one of our upcoming articles.
Expiry
Historic password advice is to change on a regular basis. The benefit of this process is questionable with users often reusing the same password but incrementing a final digit by one every change. Cybercriminals know this, so if they have an old password that doesn’t work they will try incremental numbers.
When comparing to the impact on users there is an argument that passwords should not be changed on a regular basis. These arguments are detailed here; Time to rethink mandatory password changes | Federal Trade Commission (ftc.gov)
Users should always change a password if they fear that it has been compromised, or is known.
Password Manager
The average user, with around 100 unique passwords of 15 or more characters, would be forgiven for not remembering each one.
The best way to manage passwords is for users to implement a password manager. Many are available so which should you choose? Much like antivirus sotware, the software should be deployed business-wide and be centrally managed.
Central management of passwords means that you can enforce your business password policy to your team.
Popular products that offer business password management include Keeper, Dashlane, Lasspass, and N-able Passportal.
Enforcement and policy
One could argue that a user with weak password security is equivalent in negligence to leaving a window open when they go home at night, leaving the companie’s assets vulnerable to theft.
The most important task is to define the password policy and communicate that with your team, therefore setting the expectations.
When creating policies you should consider including the following;
- Ensure all devices and services with business are protected with a password
- Passwords length, complexity, and uniqueness;
- Implement two factory authentication wherever possible;
- Use of business email only for business services, and not personal shopping accounts;
The banning of sharing passwords with internal staff, or anyone external
Unfortunately, it’s not always possible for us to monitor or define the length of complexity of passwords in use, although using a Password Manager, as above, does help. We can, however, provide simulated phishing to identify those users who are more prone to clicking inappropriate links and providing information.
You can also check whether a business email address has been breached by checking this website; Have I Been Pwned: Check if your email has been compromised in a data breach
One final note on passwords. The most important password to protect is the email password as this is often used to reset other passwords.








