Introduction
In our last article, we discussed the massive growth in cyber breaches, due partly to the increasing number of websites used by individuals and businesses and compounded by poor password practices.
Today, we discover how you can better protect the data you and your staff rely on by implementing Multi-Factor Authentication.
Research shows that every service that doesn’t use Multi-Factor Authentication will have some breach or compromise during the year. No matter how diligently you manage your passwords, your data is at greater risk without it.
In 2018, the National Cyber Security Centre posted advice to users on how to protect their Office 365 account, which focussed entirely on the deployment of Multi-Factor Authentication; The rise of Microsoft Office 365 compromise – NCSC.GOV.UK
Businesses and charities must have a strong authentication policy to reduce their exposure to risk.
This article looks at how to protect your business with Multi-Factor Authentication.
What is Multi-Factor Authentication?
Multi-Factor Authentication (or 2FA) means authenticating access to a service by at least two of the following;
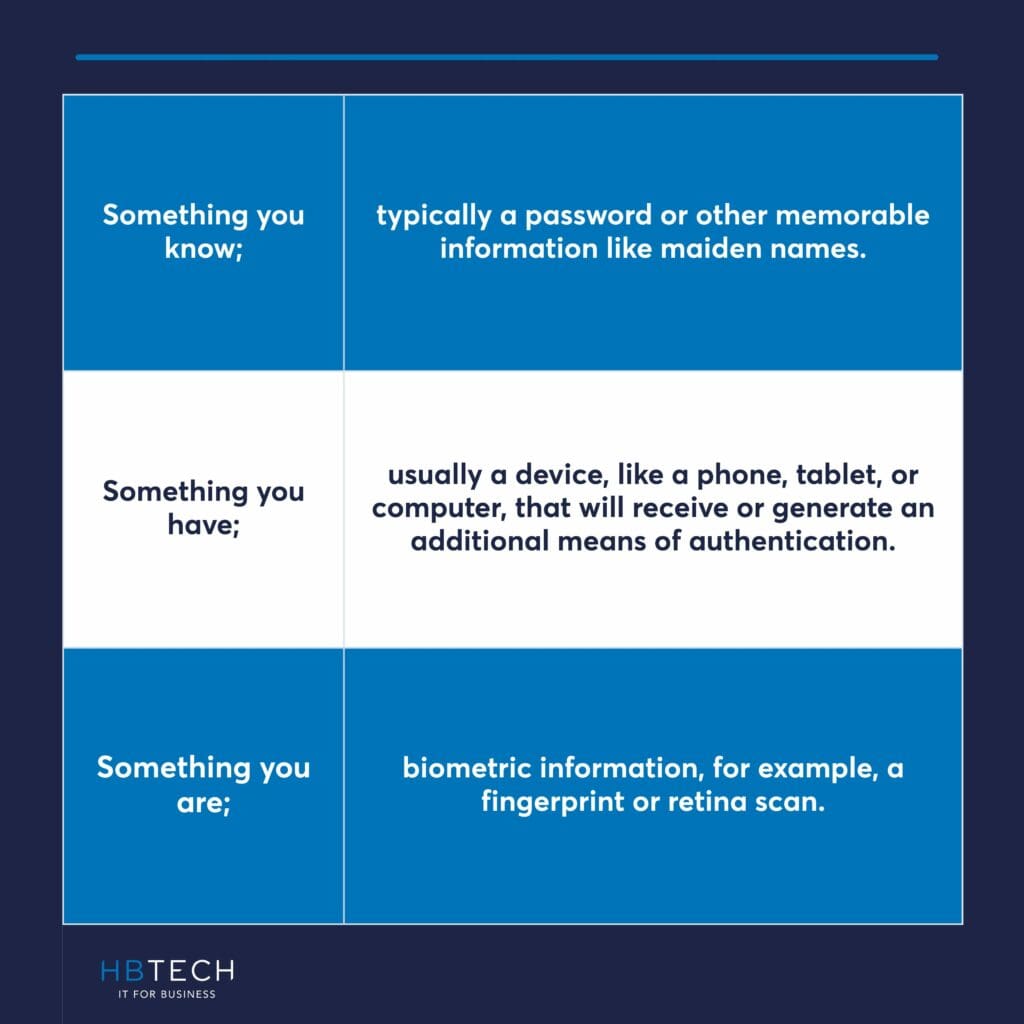
‘Something you know’ is typically a password but can also include other memorable information like maiden names. Note that entering a password followed by a memorable word is not Multi-Factor Authentication. That is something you know, followed by another thing you know.
‘Something you have’ is usually a device, like a phone, tablet, or computer, that will receive or generate an additional means of authentication.
Finally, ‘something you are’ introduces biometric information, for example, a fingerprint or retina scan.

However, we’ll see that not all secondary authentication methods are equally secure.
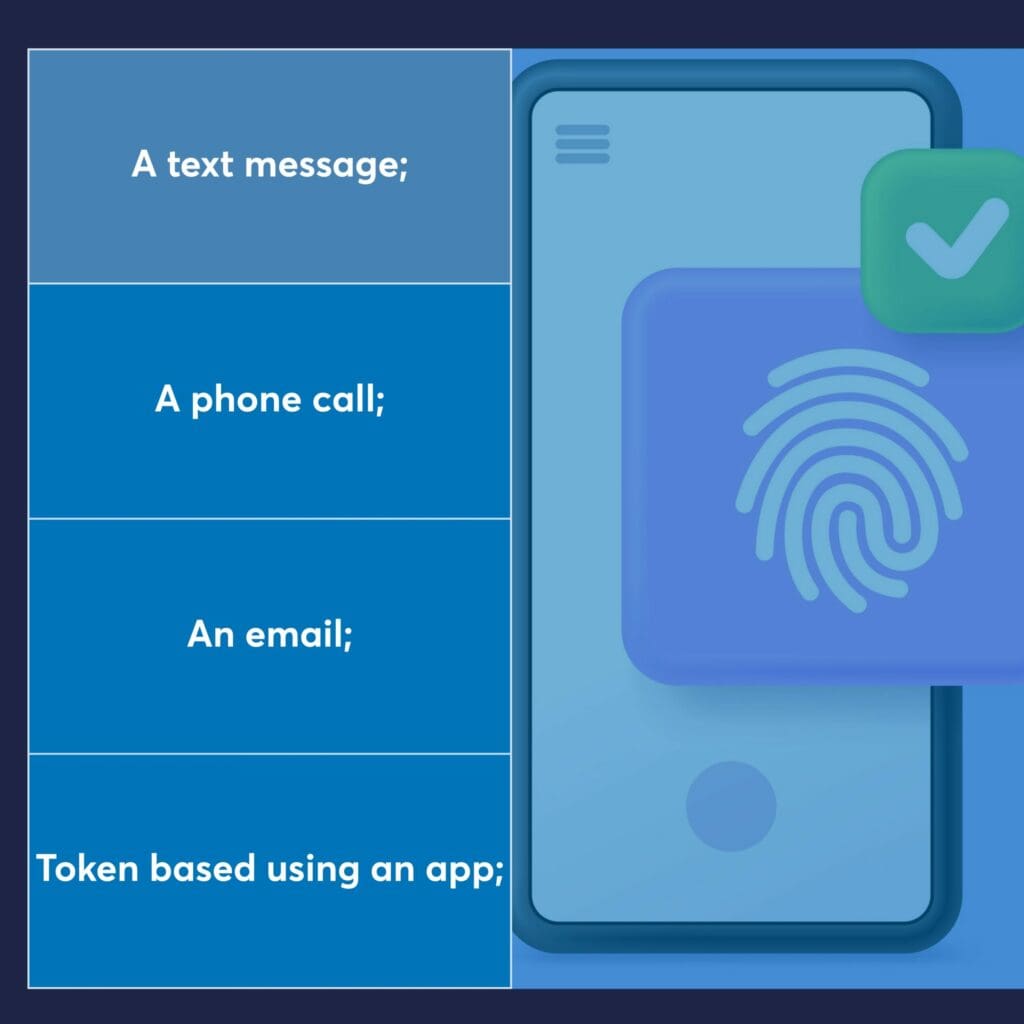
Something you have
The delivery or generation of a secondary authentication method on a device includes;
Recognising that not all these methods are equal in keeping your data secure is important. For example, in 2018, Reddit was compromised when a SIM swap meant that a hacker received the text authentication to an account, which allowed them to gain access to some of Reddit’s data.
Moreover, text messages are sent unencrypted, and with the right equipment and knowledge, a text message can be intercepted.
Where a mobile phone is unavailable, it is often possible to select a phone call as the additional means of authentication. However, it’s not always possible to control who will pick up the call, especially in an office environment. Telephone calls can also be intercepted.
Token-based Authentication
Token-based authentication has the potential to be the safest method to authenticate users accessing an account; however, even here, not all solutions are equal.
Token-based authentication requires the user to install an app on a device that will receive ‘a push’ notification or generate a code, usually six digits long, to authenticate the user.
Evidence shows, however, that at least some significant breaches have occurred where users have ‘push fatigue’ and are so used to accepting requests that they do it automatically. To counter this, WatchGuard will release a version of their token-based app that uses geolocation, where a push will automatically be blocked where a user has authenticated in the UK, and half an hour later, an authentication request comes from, say, China. Likewise, a request will be denied if the service is in the UK and the push comes from Russia. It’s not possible to be in both places simultaneously.
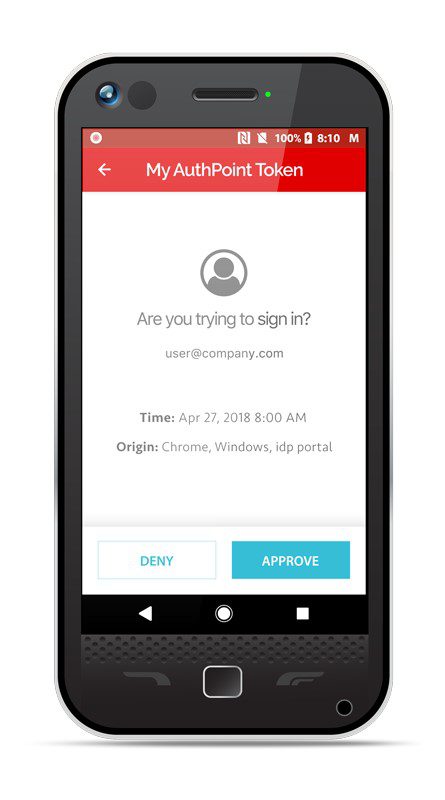

Alternatively, an app will generate a six-digit code, a one-time password (OTP), that can be entered when logging in to the service. Code generation and entry is more work for the user, but more secure as the user has to enter a specific code rather than clicking ‘allow’ or ‘deny’.
Some authenticator services rely solely on an algorithm and a date/time stamp which means authentication can be cloned to another device. The safest apps are those that tie authentication into a unique characteristic of the device so that it can’t be cloned to other devices.
So now we have our authentication method; which services should be activated?
Which accounts should be Authenticated?

Malwarebytes suffered a breach when a dormant account without multi-factor authentication was compromised, and the account was used to send malware links internally throughout the network.
Not every service will have Multi-Factor Authentication enabled, but wherever it is, we recommend it’s enabled for all users.
What should I do now?
We recommend you review all services that users log into and deploy Multi-Factor Authentication where possible. Ideally, you should implement a strong authenticator app service like WatchGuard Authpoint that has all the recommended features above.
For more information about WatchGuard Authpoint see: About AuthPoint; Multi-Factor Authentication
If you would like to discuss this further, please don’t hesitate to contact us, we’d love to hear from you.








